Secure Password Storage: Expert Guidelines
In the realm of digital security, safeguarding user credentials stands as a paramount concern. As organizations navigate the ever-evolving landscape of cybersecurity, the question of how to store passwords in a database securely becomes a critical focus. This article delves into expert guidelines and proven methodologies that ensure the confidentiality and integrity of user data.
By implementing the best practices detailed here, you can fortify your systems against unauthorized access and data breaches, ultimately fostering a more secure digital environment.
Optimal Method for Storing Passwords in Database
Safeguarding user information stands as the cornerstone of trust in digital technologies amid the ever-evolving landscape of cybersecurity. An essential element of this trust involves the secure storage of credentials within databases.
In the context of an increasingly complex digital environment and ever more sophisticated threats, understanding the nuances of safe passcode storage has become imperative for any organization entrusted with safeguarding user data. This article delves deeply into numerous strategies and optimal methodologies, underscoring the paramount significance of fortifying passcode protection within databases to preserve the confidentiality and integrity of user accounts.
The Cruciality of Secure Password Storage
User passcodes act as sentinels guarding the gates to confidential information, making the methodology of their storage a pivotal task. Inadequate security measures can lead to unauthorized access, data breaches, and irreparable harm to an organization’s reputation. In this context, two primary technologies – hashing and salting – play a pivotal role in the realm of secure storage.
Hashing: Transforming Passcodes into Cryptographic Secrets
Hashing involves transforming a passcodeinto a fixed-length string of characters using a mathematical algorithm. This process ensures that even if a hashed passcode is compromised, the original code remains difficult to discern. Widely utilized hashing algorithms like SHA-256 and bcrypt deliberately introduce resource-intensive computations, rendering them resistant to hacking attempts.
Salting: Adding a Layer of Unpredictability
Salting enhances passcode resilience by introducing a random number before encryption. Each user’s code is combined with a unique salt, thwarting attackers’ ability to reverse-engineer hashed passcodes using precomputed rainbow tables. This technology significantly elevates the security threshold against malicious actors attempting unauthorized access.
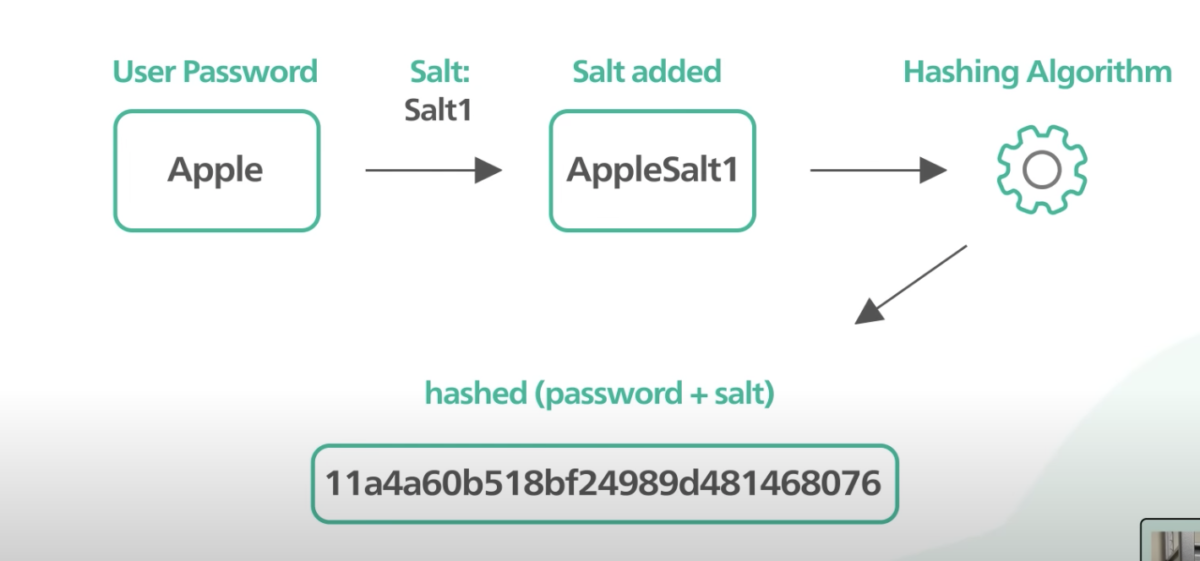
Best Practices for Secure Storage
Encourage users to create robust passcodes by implementing stringent policies. Such policies may mandate a combination of uppercase and lowercase letters, digits, and special characters. Additionally, setting a minimum length and prohibiting common passcodes fortifies defense against brute-force and dictionary attacks.
- Key Derivation Functions (KDFs). Employ key derivation functions like bcrypt and Argon2, specifically designed for secure storage. These functions encompass salting and multiple rounds of hashing, bolstering resilience against attacks;
- Abandon plaintext storage. Storing passcodes in plaintext is a cardinal sin of cybersecurity. Always hash and salt passcodes before storing them in databases. This ensures that even if a database is breached, actual passcodes remain concealed;
- Stay vigilant about the relevance of hashing algorithms. As computational power advances, older hashing algorithms become increasingly vulnerable to attacks. Regularly update hashing algorithms within your system to mitigate potential vulnerabilities;
- Elevate security through two-factor authentication (2FA). Implementing 2FA provides an additional layer of protection. Even if passcodes are compromised, assailants cannot access accounts without an additional authentication factor, such as an SMS code or an authentication app token;
- Extend encryption to sensitive data. Don’t limit encryption to passcodes; encrypt other confidential data stored in databases. This offers an extra layer of safeguarding, ensuring that even in the event of a breach, compromised data remains indecipherable without an encryption key.
Also, regularly conduct audits and vulnerability assessments to detect hidden weaknesses in the system. Swiftly addressing vulnerabilities enhances the resilience of the security infrastructure.
Implementing Robust Storage Protocols
Ensuring secure passcode storage isn’t just a technical obligation, it’s an ethical commitment to fostering user trust and data integrity. By employing reliable hashing, salting, and encryption methods, organizations and developers can bolster their defenses against unauthorized access and data breaches.
| Step | Action |
|---|---|
| 1. | Generate a unique salt for each user. |
| 2. | Concatenate the salt with the user’s passcode. |
| 3. | Hash the combined value using a robust hashing algorithm. |
| 4. | Store the resulting hash and the associated salt in the database. |
Verification Procedure:
| Step | Action |
|---|---|
| 1. | Retrieve the hashed passcode and salt from the database based on the user’s credentials. |
| 2. | Concatenate the salt with the provided passcode during login. |
| 3. | Hash the combined value and compare it with the stored hashed passcode. |
| 4. | Grant access only if the computed hash matches the stored hash. |
Maintaining best practices, staying abreast of security paradigms, and subjecting systems to regular audits are cornerstones of maintaining the security of database ecosystems. Upholding the sanctity of user passcodes is not only a legal requirement but also a testament to an organization’s dedication to creating a secure digital landscape in the era of cyber challenges.
Can User Credentials Be Stored in a Database?
Indeed, user passcodes can be stored in a database, but the manner in which they are stored is crucial for safeguarding user accounts and confidential information. Storing passcodes as plain text poses significant security risks, making user data vulnerable to hacking attempts. Instead, secure methods such as hashing and salting should be employed, enhancing password protection.
Hashing involves converting a passcode into a fixed-length string of characters using a mathematical algorithm. This process ensures that even if a hashed passcode is compromised, the original password remains difficult to discern. Salting provides an extra layer of security by introducing a random value before hashing, unique to each user.
When implementing password storage in a database, adhering to best practices is imperative: employing robust cryptographic hashing algorithms (such as bcrypt or Argon2), employing unique salts for each user, and updating security measures periodically to align with advances in computational power and protection technologies. This way, even in the event of a breach, the impact on user data can be minimized.
How Are User Passwords Securely Stored in a Database?
User passcodes are typically stored in databases using secure technologies that protect confidential information. The goal is to prevent unauthorized access to original passwords even if the database is compromised. Here’s a general approach to securely storing user access keys in a database:
- Hashing: When a user creates or updates their access key, it is transformed into a fixed-length string of characters using a cryptographic hash function. This converts the key into a seemingly random sequence of characters, making it challenging to reverse-engineer the original access key from the hash. Popular hash functions include SHA-256, SHA-3, and bcrypt;
- Salting: To further enhance security, a unique random value known as “salt” is generated for each user. Before hashing, the salt is combined with the user’s access key. Salting is crucial to prevent attackers from using precomputed tables (rainbow tables) to swiftly guess access keys. The uniqueness of the salt for each user means that even if two users have the same password, their hashes will look entirely different due to differing salts;
- Storage: The resulting hash, along with the salt (if not included in the hash), is stored in the database. The original access key is not stored. This means that even if an intruder gains access to the database, they will only see hashed access keys and salts, which are not easily reversible to their original form;
- Verification: When a user attempts to log in, the system retrieves the hash and salt associated with their username from memory. The salt is combined with the entered passcode, and the resulting hash is compared with the stored hash. If they match, access is granted.
Simplified Example of Utilizing Hash Functions
User Registration:
- The user inputs the password: “mysecretpassword.”;
- A unique salt is generated: “abcd1234.”;
- Password + salt = “mysecretpasswordabcd1234.”;
- The combined value is hashed using a hash function: “xyz9876.”.
Database Storage:
- Stored hash: “xyz9876.”;
- Stored salt: “abcd1234.”.
User Login:
- The user provides the password: “mysecretpassword.”;
- Retrieving the stored salt: “abcd1234.”;
- Password + salt = “mysecretpasswordabcd1234.”.
Hashing the combined value using the same hash function: “xyz9876.”
Compare the computed hash (“xyz9876”) with the stored hash (“xyz9876”).
If they match, access is granted.
Consequently, even if an intruder gains access to the database, reconstructing the original access keys will be challenging. This approach significantly enhances the security of user accounts and confidential information.
What Is the Optimal Approach for Storing User Credentials in a Database?
The best practice for storing user credentials in a database revolves around ensuring the utmost security and safeguarding user accounts and sensitive data. Below is an exhaustive guide to the recommended approach:
| Practice | Description |
|---|---|
| Hashing and Salting | – Use strong cryptographic hash functions like bcrypt, Argon2, or SHA-256.<br> – Generate a unique random salt for each user before hashing.<br> – Combine salt and password before hashing for added security. |
| Key Derivation Functions (KDFs) | – Utilize specialized KDFs like bcrypt and Argon2 designed for secure password storage. |
| Avoid Plain Text Storage | – Never store access keys in plain text or reversible encryption. Hash and salt passwords before storage. |
| Strong Password Policies | – Enforce access key policies with a mix of characters (uppercase, lowercase, numbers, special).<br> – Set a minimum passcode length requirement. |
| Regularly Update Hashing Algorithms | – Keep abreast of cryptographic algorithm advancements.<br> – Periodically update hashing algorithms to maintain security against evolving threats. |
| Two-Factor Authentication (2FA) | – Implement 2FA for an additional layer of security.<br> – Requires an extra authentication factor beyond passwords. |
| Encryption of Sensitive Data | – Consider encrypting other sensitive data in the database alongside access keys. |
| Strong Access Controls | – Limit database and password-related access to authorized personnel only.<br> – Implement role-based access controls. |
| Regular Security Audits | – Conduct routine security audits and vulnerability assessments to identify and mitigate weaknesses. |
| User Education | – Educate users about strong access key practices, avoiding reuse, and recognizing phishing attempts. |
| Use Established Libraries | – Implement password storage using trusted libraries and frameworks for secure hashing functions. |
| Data Backup and Disaster Recovery | – Include provisions for securely restoring user access keys in backup and recovery plans. |
By adhering to these recommendations, you can establish a reliable and secure passcode storage system that minimizes the risk of unauthorized access and data breaches while maintaining your users’ trust.
In Conclusion
In the intricate tapestry of modern cybersecurity, the significance of secure password storage is immeasurable. As the digital world expands and its interconnectivity intensifies, custodians of data must don armor and employ rigorous protective measures to uphold the integrity of user accounts and confidential information.
This journey through the labyrinth of secure passcode storage strategies has unveiled the indispensable role of hashing, salting, and encryption in fortifying digital fortresses against the relentless onslaught of cyber threats.
On this path, the abandonment of plain text storage becomes a symbolic act of defiance against potential breaches, safeguarding the sanctity of user data. The ritual of regular security audits stands as a vigilant guardian, ensuring the detection and elimination of vulnerabilities before malevolent actors can exploit them.
The password verification procedure, represented as a symmetrical table, embodies a meticulous dance of checks and balances executed when a user attempts to enter the system. This systematic protocol underscores the gravity of user trust and data integrity, reminding us that the keys to digital citadels must be handled with utmost care.





Leave a Reply